acl filter commands
Priorities are specified for each. Examples Create a rule in IPv4 basic ACL 2000 to deny the packets from any source IP subnet but 100008 172170016 or 1921681024.
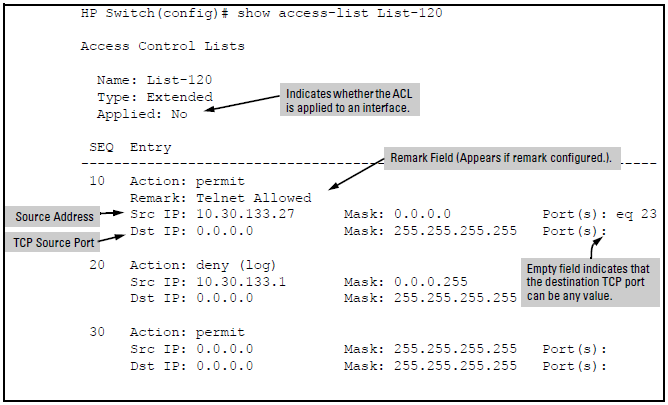
Viewing Acl Configuration Data
This command creates IP ACLs and enters the IP Access-list configuration mode.
. An IP ACL applied to a Layer 2 interface filters only the IPv6 packets. The security descriptor contains the access control lists ACLs of the resource. Command filter A filter local to the command that is active only while the command is running.
UPPER LOWER PROPER Changes the case of a character string. We assigned the number 10 to this ACL. IP ACL MAC-IP ACL and IPv6 ACL.
The no command disables the deny-preemption function. The full syntax of the standard ACL command is as follows. Router config access-list 1-99 permit deny source-addr source-wildcard The breakdown of the different parts of the syntax is as follows.
- It is a numerical argument. The first statement denies all traffic from the network 10000. The IPv6 access lists are used for traffic filtering based on source and destination addresses IPv6 option headers and optional upper-layer protocol type information for finer granularity of control.
Change the ACL type. Command filters Output typename Limits on how many records will be processed More tab Key fields The fields against which the command is run. Filter the table according to the action profile name.
The ipv6 access-list command is similar to the ipv4 access-list command except that it is IPv6-specific. Denypermit MAC ACL rule seq-number permit. Following is the limitation for this command to be applicable to Layer 2 interfaces.
The access-list global configuration command defines a standard ACL with a number in the range of 1 to 99. We used the next two commands to create a standard access list with two statements. This command allows us to create a standard-numbered ACL and an extended-numbered ACL.
This is a global configuration mode command. Set the object filter for filtered ACLs. Denypermit MAC ACL rule seq-number permit.
The access control list should be defined prior to the binding action. Set addition and deletion rights. The ACL specifies the permissions that users and user groups have to access the resource.
No ip access-list extended. UPPERdave DAVE LOWERDAVE dave PROPERDAVE. The second statement allows all traffic from the network 20000.
Router config access-list ACL_ permitdeny conditions. Use undo packet-filter to remove an ACL from a zone pair. If you are adding an ACL all other fields default to blank.
The access-list command. The Type field defaults to the type you selected on the Edit ACL panel. IPv6 Software Access Control List ACL Commands Hardware ACLs are applied directly to interfaces or are used for Quality of Service QoS.
The full syntax of the standard ACL command to filter a specific host is as follows. Beginning in Windows PowerShell 30 you can use the. The command to permit all addresses is.
Certain commands can only be run against specific field types either character numeric or date. IPv6 access list must have been created before enabling the access list for the inbound IPv6 packets. Enable the deny-preemption function.
This cmdlet is only available on the Windows platform. Specifies the IPv6 ACL type. Ip access-list extended.
An Access Control List is one filter or a sequence of filters that are applied to an interface to either block or pass or when using QoS apply priority to packets that match the filter definitions. The no form of the command deletes the IP access-list. Display summary of the action list.
Now here is the syntax used for creating a standard access list. The configuration for a standard ACL on a Cisco router is as follows. Display summary of the action list.
No ACL is applied to a zone pair to filter packets. With the extended ACL you can also block source and destination for single hosts or entire networks. With the above understanding we will now show you how to create a standard access list.
Access-list deny-preemption no access-list deny-preemption Function. You can also use an extended ACL to filter traffic based on protocol information IP ICMP TCP UDP. Function Description Example.
If you are editing an ACL the fields contain the values set last time the ACL was modified. ACL filter behavior permit or deny conflicts when a data packet matches multiple types of the four ACLs. Filter the table according to the action profile name.
This command uses the following syntax. The access control list should be defined prior to the binding action. The counting keyword in this command enables match counting specific to rules and the hardware-count keyword in the packet-filter command enables match counting for all rules in an ACL.
Packet-filter ipv6 acl-number name acl-name undo packet-filter ipv6 acl-number name acl-name Default. We used the first two commands to enter global configuration mode. The Get-Acl cmdlet gets objects that represent the security descriptor of a file or resource.
Access List In And Out Explained Archives Networkustad
Ch 5 Access Control Lists Part 1 Acl Fundamentals Ppt Download
Catalyst 4500 Series Switch Software Configuration Guide 12 2 53 Sg Configuring Network Security With Acls Cisco Catalyst 4500 Series Switches Cisco
Acl Configuration Ne40e V800r011c10 Configuration Guide Ip Services 02 Huawei
Chapter 4 Access Control Lists Ppt Download
Standard Access List Acl Full Explanation And Configuration Ccdtt
Basic Concepts And Fundamentals Of Acls
Vacl Vlan Access List Lab Using Cisco Catalyst Switch Youtube
Basic Concepts And Fundamentals Of Acls
Acl Configuration Ne40e V800r011c10 Configuration Guide Ip Services 02 Huawei
Viewing Acl Configuration Data
Chapter 4 Access Control Lists Ppt Download
7 2 2 6 Lab Configuring And Modifying Standard Ipv4 Acls Topology Addressing Table Device Studocu
Comments
Post a Comment